Using AmneziaWG 2.0 Protocol on Self-Hosted Servers
General Information
The new AmneziaWG 2.0 protocol can disguise VPN traffic as common network protocols (for example, QUIC, DNS, and others). This makes VPN connections harder to detect and block by Deep Packet Inspection (DPI) systems.
The AmneziaWG 2.0 protocol is supported in the AmneziaVPN app version 4.8.12.7 and later. In most cases, no additional server-side steps are required—most servers are already compatible. See: VPS requirements.
Starting from AmneziaVPN 4.8.12.7, an existing AmneziaWG version 1.0 protocol installation on the server is shown as AmneziaWG Legacy.
Key changes in the AmneziaWG 2.0 protocol compared to 1.5:
- added parameters
S3andS4 - added range support for
H1–H4: values are now chosen randomly and should not overlap - removed parameters
j1-j3anditime, as they were deemed redundant
Note: compared to the AmneziaWG 1.0 protocol, AmneziaWG 1.5 introduced the I1-I5 parameters, which are also used in the AmneziaWG 2.0 protocol.
Install the AmneziaWG 2.0 Protocol
To connect using the AmneziaWG 2.0 protocol, install it on your server:
- Update AmneziaVPN to 4.8.12.7 or later from the downloads page (mirror).
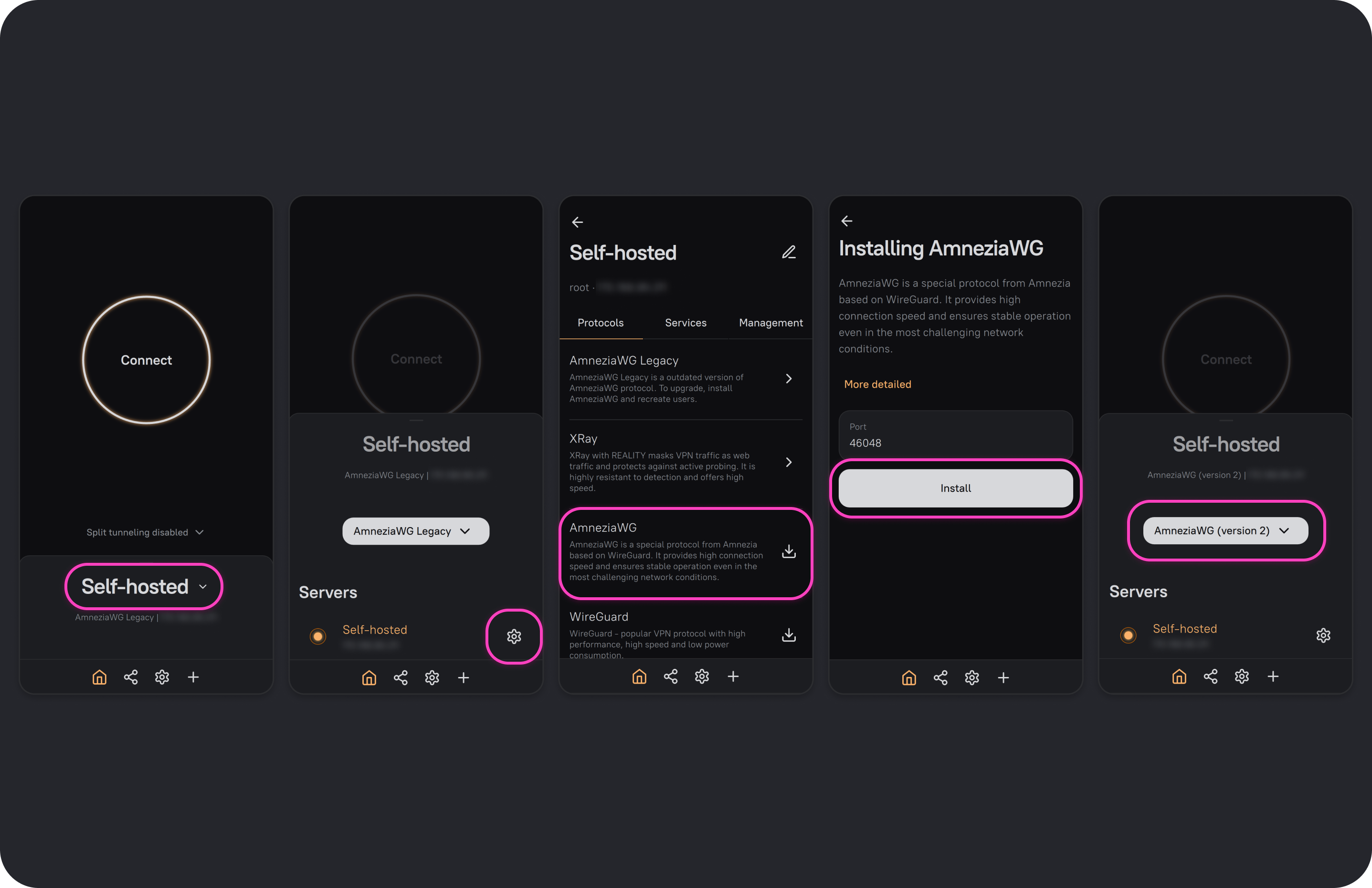
- Open the AmneziaVPN app and click any connection name.
- Click ⚙️ (gear icon) to the right of your server connection to open the list of available protocols.
- Click the 📥 icon next to the AmneziaWG protocol, then click Install.
After installation, the AmneziaWG 2.0 protocol will be available in the connection settings—you can connect immediately and share VPN access using the new protocol.
In most cases, you don’t need to change AmneziaWG 2.0 settings after installation—connections typically work out of the box for both full-access and guest-access devices.
FAQ
Do I need to generate new configuration files/keys to connect using the AmneziaWG 2.0 protocol?
Yes.
In AmneziaVPN 4.8.12.7 and later, an existing AmneziaWG 1.0 protocol installation on the server will be shown as AmneziaWG Legacy, with its own configuration files and keys that will continue to work. When you install the AmneziaWG protocol, version 2.0 is used by default—this is a different protocol, and you’ll need to generate new guest configuration files/keys to connect.
Can I upgrade an existing AmneziaWG 1.0 connection to version 2.0?
No.
You’ll need to generate a new configuration file or key for the new protocol.
Can I connect using the AmneziaWG 2.0 protocol in an older version of AmneziaVPN?
No.
If you create a guest connection for the AmneziaWG 2.0 protocol in AmneziaVPN versions earlier than 4.8.12.7, it won’t work. If you create a full-access connection in an older version of AmneziaVPN, the AmneziaWG 2.0 protocol won’t be shown even if it’s installed on the server.
Using the AmneziaWG 1.5 Protocol If the AmneziaWG 2.0 Protocol Is Unavailable
If you can’t update to AmneziaVPN 4.8.12.7 or later, and the AmneziaWG 1.0 protocol is installed on your server, you can improve its resistance to blocking by setting the I1 parameter on the devices that connect to the server via the AmneziaWG 1.0 protocol.
How to Configure
-
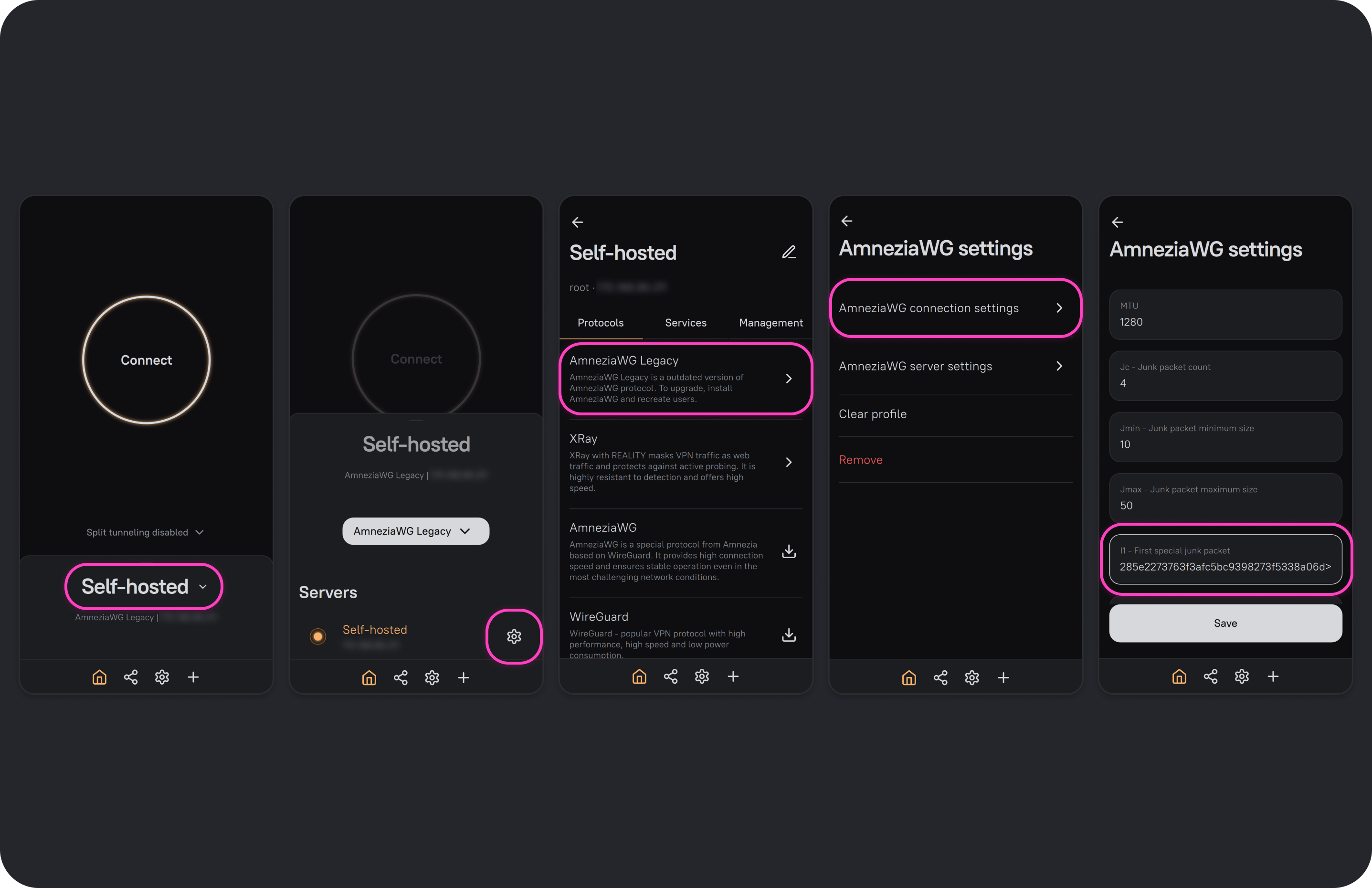
Open the AmneziaVPN app and click any connection name.
-
Click ⚙️ (gear icon) to the right of your server connection.
-
From the list of installed protocols, select AmneziaWG Legacy (or AmneziaWG, depending on which protocol version you’re configuring), then open AmneziaWG connection settings.
-
Find the field I1 - First special junk packet and paste the following obfuscation packet:
<b 0xc70000000108ce1bf31eec7d93360000449e227e4596ed7f75c4d35ce31880b4133107c822c6355b51f0d7c1bba96d5c210a48aca01885fed0871cfc37d59137d73b506dc013bb4a13c060ca5b04b7ae215af71e37d6e8ff1db235f9fe0c25cb8b492471054a7c8d0d6077d430d07f6e87a8699287f6e69f54263c7334a8e144a29851429bf2e350e519445172d36953e96085110ce1fb641e5efad42c0feb4711ece959b72cc4d6f3c1e83251adb572b921534f6ac4b10927167f41fe50040a75acef62f45bded67c0b45b9d655ce374589cad6f568b8475b2e8921ff98628f86ff2eb5bcce6f3ddb7dc89e37c5b5e78ddc8d93a58896e530b5f9f1448ab3b7a1d1f24a63bf981634f6183a21af310ffa52e9ddf5521561760288669de01a5f2f1a4f922e68d0592026bbe4329b654d4f5d6ace4f6a23b8560b720a5350691c0037b10acfac9726add44e7d3e880ee6f3b0d6429ff33655c297fee786bb5ac032e48d2062cd45e305e6d8d8b82bfbf0fdbc5ec09943d1ad02b0b5868ac4b24bb10255196be883562c35a713002014016b8cc5224768b3d330016cf8ed9300fe6bf39b4b19b3667cddc6e7c7ebe4437a58862606a2a66bd4184b09ab9d2cd3d3faed4d2ab71dd821422a9540c4c5fa2a9b2e6693d411a22854a8e541ed930796521f03a54254074bc4c5bca152a1723260e7d70a24d49720acc544b41359cfc252385bda7de7d05878ac0ea0343c77715e145160e6562161dfe2024846dfda3ce99068817a2418e66e4f37dea40a21251c8a034f83145071d93baadf050ca0f95dc9ce2338fb082d64fbc8faba905cec66e65c0e1f9b003c32c943381282d4ab09bef9b6813ff3ff5118623d2617867e25f0601df583c3ac51bc6303f79e68d8f8de4b8363ec9c7728b3ec5fcd5274edfca2a42f2727aa223c557afb33f5bea4f64aeb252c0150ed734d4d8eccb257824e8e090f65029a3a042a51e5cc8767408ae07d55da8507e4d009ae72c47ddb138df3cab6cc023df2532f88fb5a4c4bd917fafde0f3134be09231c389c70bc55cb95a779615e8e0a76a2b4d943aabfde0e394c985c0cb0376930f92c5b6998ef49ff4a13652b787503f55c4e3d8eebd6e1bc6db3a6d405d8405bd7a8db7cefc64d16e0d105a468f3d33d29e5744a24c4ac43ce0eb1bf6b559aed520b91108cda2de6e2c4f14bc4f4dc58712580e07d217c8cca1aaf7ac04bab3e7b1008b966f1ed4fba3fd93a0a9d3a27127e7aa587fbcc60d548300146bdc126982a58ff5342fc41a43f83a3d2722a26645bc961894e339b953e78ab395ff2fb854247ad06d446cc2944a1aefb90573115dc198f5c1efbc22bc6d7a74e41e666a643d5f85f57fde81b87ceff95353d22ae8bab11684180dd142642894d8dc34e402f802c2fd4a73508ca99124e428d67437c871dd96e506ffc39c0fc401f666b437adca41fd563cbcfd0fa22fbbf8112979c4e677fb533d981745cceed0fe96da6cc0593c430bbb71bcbf924f70b4547b0bb4d41c94a09a9ef1147935a5c75bb2f721fbd24ea6a9f5c9331187490ffa6d4e34e6bb30c2c54a0344724f01088fb2751a486f425362741664efb287bce66c4a544c96fa8b124d3c6b9eaca170c0b530799a6e878a57f402eb0016cf2689d55c76b2a91285e2273763f3afc5bc9398273f5338a06d> -
Click the Save button to apply the settings.
This device will now connect to the VPN server with traffic obfuscated to look like QUIC.
If you’re changing the connection settings on Windows, also set the Itime parameter to 0.
How to Extract a Protocol Signature for AmneziaWG Manually
This section will guide you through the process of manually finding and extracting a network protocol signature to use with the AmneziaWG protocol.
You will need Wireshark app, which can be downloaded from the official website.
Preparation
-
Install and launch Wireshark.
-
In the Wireshark main window, select the network interface currently handling your internet traffic.
-
Click the Start capturing packets button to begin capturing network traffic.

Finding a Protocol Signature (Using QUIC as an Example)
Let's illustrate how to find a signature using the popular UDP-based QUIC protocol as an example:
-
After starting packet capture, enter the name of the desired protocol (e.g.,
quic) into the Wireshark filter field.
If you haven't yet selected a specific protocol and want to explore available UDP protocols, simply type
udpinto the filter field. -
From the list of captured packets, select the packet you want to use for obfuscation.
Tip:
It's recommended to select initial or final packets from a session, as they tend to be most effective for masking VPN traffic. -
Right-click on the selected packet and choose Copy → …as Hex Stream.

You'll end up with a HEX-formatted string like this:
c70000000108ce1bf31eec7d93360000449e227e4596ed7f75c4d35ce31880b4133107c822c6355b51f0d7c1bba96d5c210a48aca01885fed0871cfc37d59137d73b506dc013bb4a13c060ca5b04b7ae215af71e37d6e8ff1db235f9fe0c25cb8b492471054a7c8d0d6077d430d07f6e87a8699287f6e69f54263c7334a8e144a29851429bf2e350e519445172d36953e96085110ce1fb641e5efad42c0feb4711ece959b72cc4d6f3c1e83251adb572b921534f6ac4b10927167f41fe50040a75acef62f45bded67c0b45b9d655ce374589cad6f568b8475b2e8921ff98628f86ff2eb5bcce6f3ddb7dc89e37c5b5e78ddc8d93a58896e530b5f9f1448ab3b7a1d1f24a63bf981634f6183a21af310ffa52e9ddf5521561760288669de01a5f2f1a4f922e68d0592026bbe4329b654d4f5d6ace4f6a23b8560b720a5350691c0037b10acfac9726add44e7d3e880ee6f3b0d6429ff33655c297fee786bb5ac032e48d2062cd45e305e6d8d8b82bfbf0fdbc5ec09943d1ad02b0b5868ac4b24bb10255196be883562c35a713002014016b8cc5224768b3d330016cf8ed9300fe6bf39b4b19b3667cddc6e7c7ebe4437a58862606a2a66bd4184b09ab9d2cd3d3faed4d2ab71dd821422a9540c4c5fa2a9b2e6693d411a22854a8e541ed930796521f03a54254074bc4c5bca152a1723260e7d70a24d49720acc544b41359cfc252385bda7de7d05878ac0ea0343c77715e145160e6562161dfe2024846dfda3ce99068817a2418e66e4f37dea40a21251c8a034f83145071d93baadf050ca0f95dc9ce2338fb082d64fbc8faba905cec66e65c0e1f9b003c32c943381282d4ab09bef9b6813ff3ff5118623d2617867e25f0601df583c3ac51bc6303f79e68d8f8de4b8363ec9c7728b3ec5fcd5274edfca2a42f2727aa223c557afb33f5bea4f64aeb252c0150ed734d4d8eccb257824e8e090f65029a3a042a51e5cc8767408ae07d55da8507e4d009ae72c47ddb138df3cab6cc023df2532f88fb5a4c4bd917fafde0f3134be09231c389c70bc55cb95a779615e8e0a76a2b4d943aabfde0e394c985c0cb0376930f92c5b6998ef49ff4a13652b787503f55c4e3d8eebd6e1bc6db3a6d405d8405bd7a8db7cefc64d16e0d105a468f3d33d29e5744a24c4ac43ce0eb1bf6b559aed520b91108cda2de6e2c4f14bc4f4dc58712580e07d217c8cca1aaf7ac04bab3e7b1008b966f1ed4fba3fd93a0a9d3a27127e7aa587fbcc60d548300146bdc126982a58ff5342fc41a43f83a3d2722a26645bc961894e339b953e78ab395ff2fb854247ad06d446cc2944a1aefb90573115dc198f5c1efbc22bc6d7a74e41e666a643d5f85f57fde81b87ceff95353d22ae8bab11684180dd142642894d8dc34e402f802c2fd4a73508ca99124e428d67437c871dd96e506ffc39c0fc401f666b437adca41fd563cbcfd0fa22fbbf8112979c4e677fb533d981745cceed0fe96da6cc0593c430bbb71bcbf924f70b4547b0bb4d41c94a09a9ef1147935a5c75bb2f721fbd24ea6a9f5c9331187490ffa6d4e34e6bb30c2c54a0344724f01088fb2751a486f425362741664efb287bce66c4a544c96fa8b124d3c6b9eaca170c0b530799a6e878a57f402eb0016cf2689d55c76b2a91285e2273763f3afc5bc9398273f5338a06d
How to Prepare a HEX String for Use in AmneziaVPN
After copying the hex string from Wireshark, you need to format it properly to be compatible with AmneziaWG protocol parameters.
To format the hex string correctly, do the following:
- Add the prefix
<b(with a space) before the string. - Add the prefix
0ximmediately before the hex string. - End the string with a closing character
>.
Thus, the original hex string: c70000000108ce1bf31eec7d93360000449e227e...
should look like this: <b 0xc70000000108ce1bf31eec7d93360000449e227e...>
Format Explanation:
<b ...> — indicates that this is a special binary data packet.
0x — specifies that the following characters represent hexadecimal (hex) data.
How to Configure AmneziaVPN
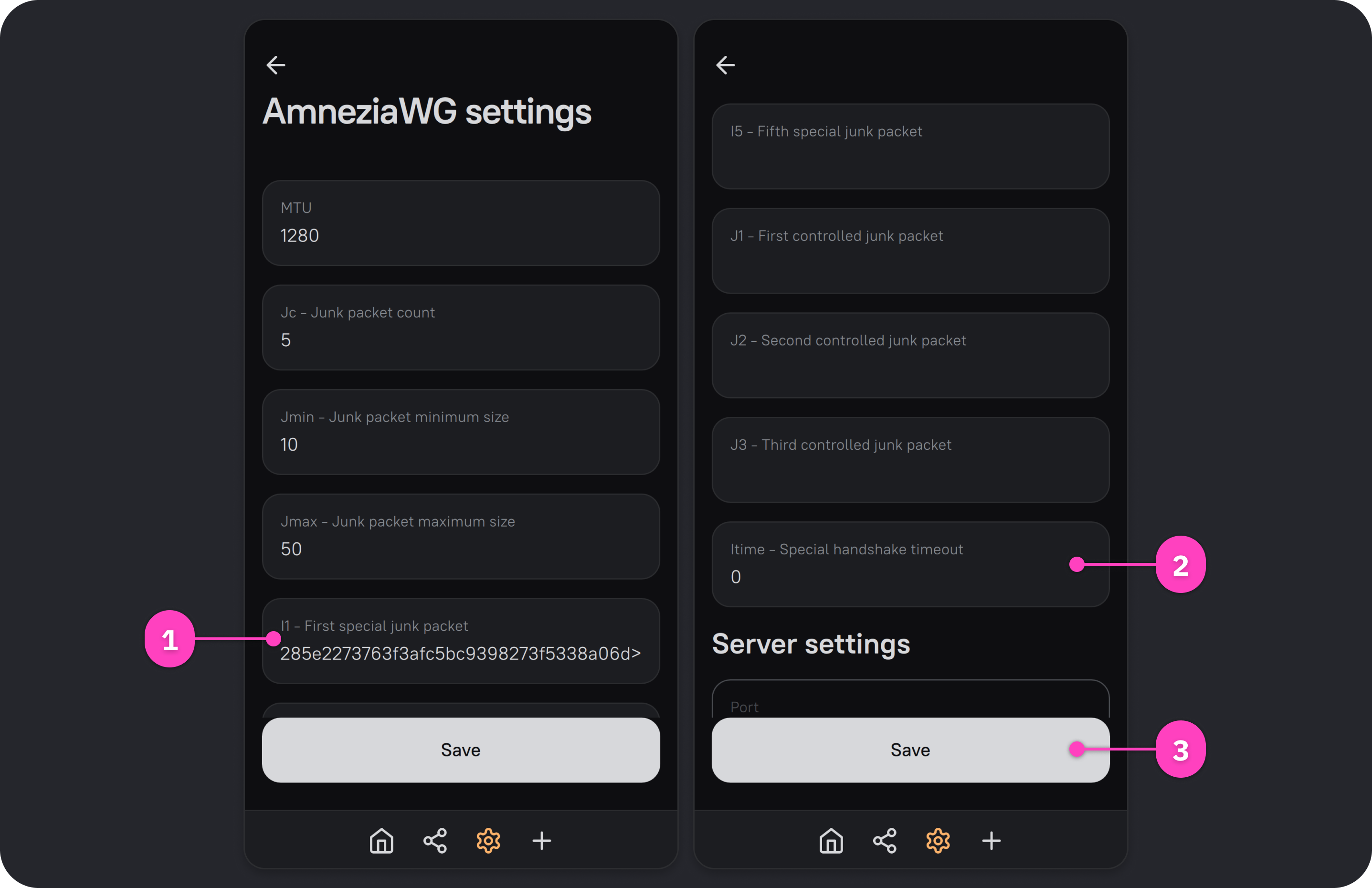
Use the formatted string to change the I1-I5 parameters on either the server or the client, depending on which AmneziaWG protocol version you use.
If the server uses the AmneziaWG 1.0 protocol (shown as AmneziaWG Legacy), you can only change I1-I5 on the client side—meaning you’ll need to update every device that connects using the AmneziaWG 1.0 protocol.
If the server uses the AmneziaWG 2.0 protocol, you can change I1-I5 on the server side so any newly generated VPN configuration file will inherit the server settings. As a result, any device for which a VPN configuration is created will connect to the VPN with the server's protocol settings. If needed, you can also override these settings on the client.
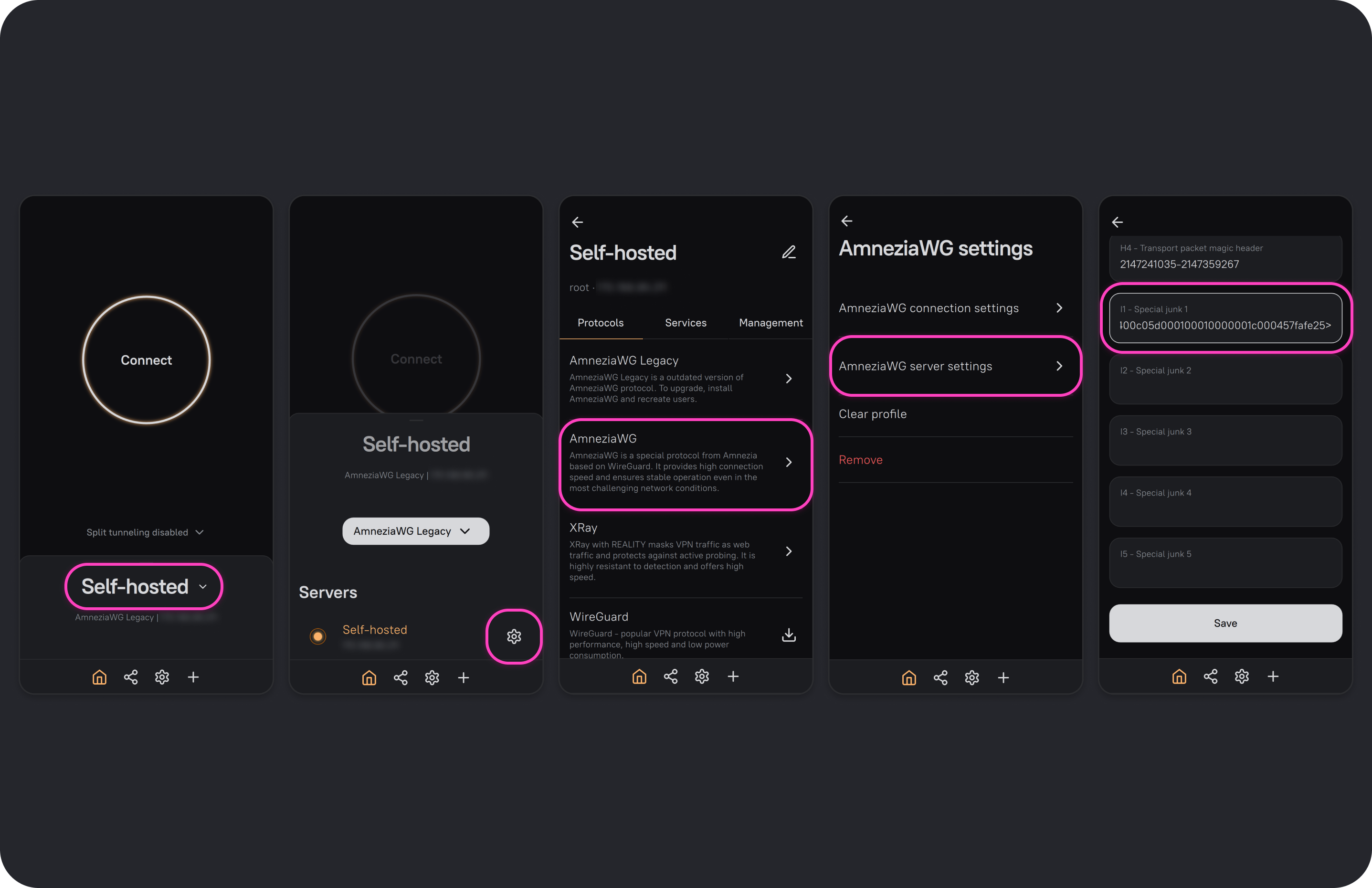
Editing Server Settings
- Open the AmneziaVPN app and click any connection name.
- Click ⚙️ (gear icon) to the right of your server connection.
- From the list of installed protocols, select the AmneziaWG protocol, then open AmneziaWG server settings.
- Find I1 - Special junk 1, paste the formatted string
<b 0xHEX>, and click Save.
Now any newly generated VPN configuration file or key will use the chosen obfuscation.
Editing Connection Settings
- Open the AmneziaVPN app and click any connection name.
- Click ⚙️ (gear icon) to the right of your server connection.
- From the list of installed protocols, select AmneziaWG Legacy or AmneziaWG (depending on which protocol version you’re configuring), then open AmneziaWG connection settings.
- Find I1 - First special junk packet, paste the formatted string
<b 0xHEX>, and click Save.
This device will now connect to the VPN server with the chosen obfuscation.
